Top 10 Use Cases for Horizon Scanning in Financial Services

Horizon scanning is becoming finance’s early warning system, giving compliance teams the foresight to anticipate regulation, risks, and market shifts before they hit. Used well, it turns reactive control functions into strategic enablers.
Not long ago, foresight in finance meant quarterly forecasts and annual risk assessments. Today, it means parsing obscure policy memos from Brussels, flagging new AI rules before the ink is dry, and fielding alerts from five regulators before breakfast.
The urgency is hard to ignore. Global regulators issued more, and that number has only trended upward since. Generative AI is redrawing the competitive map. ESG rules are being rewritten mid-flight. A social media rum or can spark a bank run in hours.
Horizon scanning is quickly becoming an imperative for financial institutions, across the enterprise structure.
1. Regulatory Compliance & Change Management
The volume of change has outgrown manual tracking. Horizon scanning lets compliance work months ahead of formal deadlines.
A disciplined scanning program maintains a register fed by consultation papers, enforcement actions, technical standards, and supervisory letters. Each entry is tagged with scope, impact rating, owner, due date, and downstream control changes. Weekly review meetings decide whether to start implementation on draft texts (for example system fields for new disclosure templates) or wait for final wording.
The result is an audit trail: how the firm identified a rule, assessed it, and built it into controls.
Seeing DORA contract compliance requirements or AI Act prohibitions before they bite allows procurement, IT, and risk teams to adjust documentation and testing cycles rather than rushing after publication. Ownership, thresholds, and closure notes keep the process defensible for supervisors.
2. Risk Management & Operational Resilience
Operational shocks spread fast.
The 2023 MOVEit exploitation drew hundreds of organizations into a single supply chain breach and exposed 93 million personal records. In 2024, UnitedHealth was targeted by a ransomware attack bringing about massive disruptions and losses of $3.09 billion. ICBC’s U.S. broker dealer unit suffered a ransomware attack in November 2023, crippling U.S. Treasury trades and causing payment delays.
A practical scanning program tracks external signals across four areas – critical vendor health, market‑infrastructure issues, cyber advisories, and geopolitics. Each signal gets a proximity score and an owner. When a trigger fires, teams run a playbook. They confirm substitution options, rehearse manual workarounds, and brief the resilience committee with dated notes.
U.S. supervisors have set clear expectations. The OCC, Federal Reserve, and FDIC issued “Sound Practices to Strengthen Operational Resilience,” which focus on delivering critical operations through disruption and on learning from incidents. The FFIEC Business Continuity Management booklet tells examiners to assess impact analyses, testing, and third‑party arrangements.
Some rules are sector‑specific. SEC Regulation SCI requires covered entities to maintain business continuity and disaster recovery plans and to coordinate testing with members. Across all facets, a common theme is emerging. The outcome should be traceable.
3. Strategic Planning & Business Development
Systems track macro releases from the Federal Reserve, rulemakings that alter business models, and competitor moves. Current items include Federal Reserve stress test scenarios and the CFPB Section 1033 open banking rule.
Horizon scanning data can also be integrated into frameworks like PESTLE analysis and scenario planning to support strategy reviews and board discussions with credible evidence.

Sample playbook
- Rule final or near‑final (1033): schedule API governance, vendor diligence, and customer‑consent design in the product stage‑gate.
- BNPL interpretive rule: update disclosures, disputes handling, and marketing review before any scale‑up.
- Fed scenario release: set macro guardrails for plan assumptions and liquidity buffers, then update planning packs.
- Competitor launch in a target segment: run a pricing and underwriting review, then decide on match, differentiate, or pause.
At the same time, flagging emerging regulatory change helps compliance teams build appropriate guardrails early. This ensures strategic initiatives launch with controls and oversight already in place.
4. Technology & Digital Transformation Monitoring
Scanning programs track different streams such as regulator actions on AI claims, federal standards for cryptography, and vendor lifecycle notices. The SEC settled cases against Delphia and Global Predictions for misleading AI marketing. That set a clear mark for what firms can say about AI.
The BIS advises financial firms to inventory and begin transition planning for quantum-resistant systems now, not after quantum computers become viable. Europol’s Quantum Safe Financial Forum urges banks to prepare even if commercial “Q‑Day” is a decade away. NIST finalized three post‑quantum cryptography standards on August 13, 2024. Firms should monitor FIPS 203, 204, and 205 updates and vendor roadmaps.
Sample playbook
- AI marketing claims: A new SEC action or speech triggers a marketing review. Legal checks disclosures and disclaimers. Model risk confirms the model inventory and documentation. Map controls to NIST AI RMF functions for governance and monitoring.
- Post‑quantum standards: A NIST release triggers a cryptography inventory. Technology teams list crypto libraries, TLS endpoints, KMS usage, and key lifetimes. They then draft a migration schedule for high‑value systems.
- End‑of‑life notices: A vendor deprecation triggers change tickets, substitution analysis, and capacity testing. Records show approvals and test results.
Technology changes and tests should reference the external signal that prompted them.
5. Market Intelligence & Competitive Analysis
Scanning programs monitor competitor filings, earnings call transcripts, rate and fee pages, investor day decks, and public product terms. They also track regulator actions that change market conduct expectations. Each item receives scores for revenue impact, conduct risk, and time to effect.
This reduces the chance of rushed repricing that creates UDAAP or fair lending issues. It also gives boards a dated rationale for why the firm matched, differentiated, or paused.
A common scenario starts with a competitor earnings call. The transcript lands in the register the same day, tagged for revenue impact and conduct risk. Treasury and product review the change in savings rates and fees. Compliance checks disclosures under TILA and UDAAP, and runs a quick fair lending screen under ECOA and Regulation B. The pricing committee meets, decides whether to match, differentiate, or pause, and records the rationale with the source link and date. Customer notices and updated rate pages are archived with counsel sign‑off.
Boards see the result as a short memo. One page ties the external signal to a choice, the customer impact, and any disclosure or control changes. Examiners who ask for evidence get the same chain – source, scoring, decision, and artifacts.
6. ESG Risk Assessment (Environmental, Social, Governance)
Horizon scanning tools track a moving rule set and turn signals into records. The SEC adopted climate disclosure rules on March 6, 2024. On March 27, 2025 it voted to stop defending the rule while litigation continued in the Eighth Circuit. The system logs each step and keeps provisional milestones instead of fixed dates. Boards then see a dated posture on which they can rely.
Bank supervisors sit in the same feed. Interagency principles on climate‑related financial risk were finalized for large institutions in October 2023. The OCC’s withdrawal in March 2025 was logged as a counter‑signal for OCC‑only banks. Each entry states whether governance scope changes or stays aligned with the Fed and FDIC.
Mandatory ESG disclosures are expanding fast. Around 29 countries now require sustainability reporting, and new EU rules under CSRD and the proposed ESG ratings regulation demand backward and forward-looking governance controls. The EBA expects banks to include short, medium, and long-term ESG risk horizons in internal governance and capital planning. Horizon scanning helps compliance teams prepare early so they meet disclosure standards from day one.
Insurers use NAIC’s TCFD‑aligned survey and state supervisor materials to shape board reporting and exam readiness. Each update becomes a register entry with a gap note and the next review date.
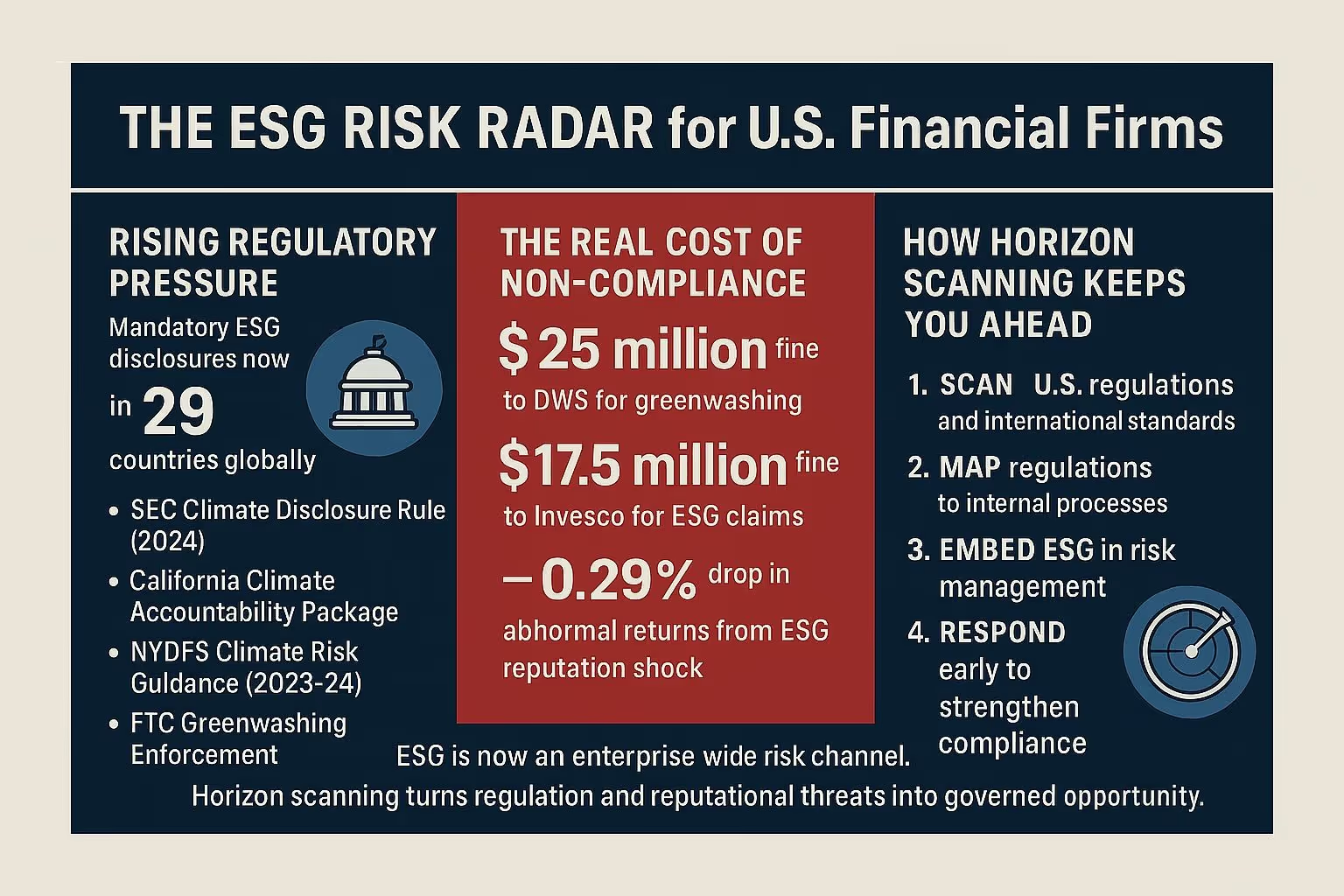
Advanced compliance programs use horizon scanning tech to ingest data from public sentiment and ESG rating developments.
The outcome is a plain evidence chain. Each ESG signal becomes a dated entry with source, owner, and a short conclusion that says what changed. Examiners and investors can follow the link from the public item to the internal redline or board note without hunting through email.
7. Business Continuity Planning (BCP)
When EquiLend went offline after a January 2024 ransomware attack, traders desperately reverted to manual workarounds. The July 2024 CrowdStrike update crash took Windows endpoints down worldwide. Each of these serve as stark reminders of how a single fault can ripple through markets.
Horizon scanning turns those shocks into early warnings. Programs watch vendor status pages and urgent patches. They track CISA ransomware guidance and sector alerts. They hold mandates such as the FFIEC business continuity handbook as the yardstick examiners use. Entries are scored for proximity and mapped to critical services before trouble starts.
The response is scripted and dated. A critical vendor bulletin triggers a change‑freeze check, a fallback drill, and a recovery test. A severe weather watch moves branch and data‑center checklists into action. Each record links the source notice to the playbook run and the test result, as CISA recommends for tested backups and recovery.
Supervisors want proof that resilience is planned and repeatable. The Business Continuity Institute reports that 52 percent of firms experienced a major disruptive event in the past five years. Institutions with mature BCP programs recover nearly five times faster than their peers.
After large events, firms close the loop. Logs include: the source alert, the score, the playbook, the test evidence, and a short lessons‑learned note.
8. Customer Sentiment Analysis & Market Research
In March 2023, Silicon Valley Bank faced $42 billion of withdrawal requests in eight hours. Social posts moved, then deposits moved.
Horizon scanning systems now treat public signals as early warnings that can shape pricing, disclosures, and service responses. They pull from structured and unstructured sources. They ingest the CFPB Consumer Complaint Database to spot sharp changes in issues such as overdraft fees, P2P errors, and card disputes. They watch mainstream coverage and high‑visibility threads that customers cite when they contact support. For registrants, they may also track materials that count as “communications with the public” under FINRA Rule 2210.
Triage is simple and fast. Records note the product, a proximity score, and the likely rule set. A jump in complaints on a fee or payment flow sends the item to legal for a UDAAP check, with draft wording and pricing options prepared in parallel.
Public claims by a broker‑dealer trigger a different route. Marketing drafts go through a Rule 2210 check before any reply or campaign. If the topic touches an issuer disclosure, counsel considers Regulation FD to avoid selective release across social channels.
The system keeps the source links, the approval, and the change record. Each entry closes with the decision, the redlined copy or notice, and the date it went live.
9. Cybersecurity Threat Intelligence
The SEC’s 2023 rule requires public companies to disclose a material cyber incident on Form 8‑K within four business days of the materiality determination. Scanning tools are used to flag early signals to tighten controls and inform that call.
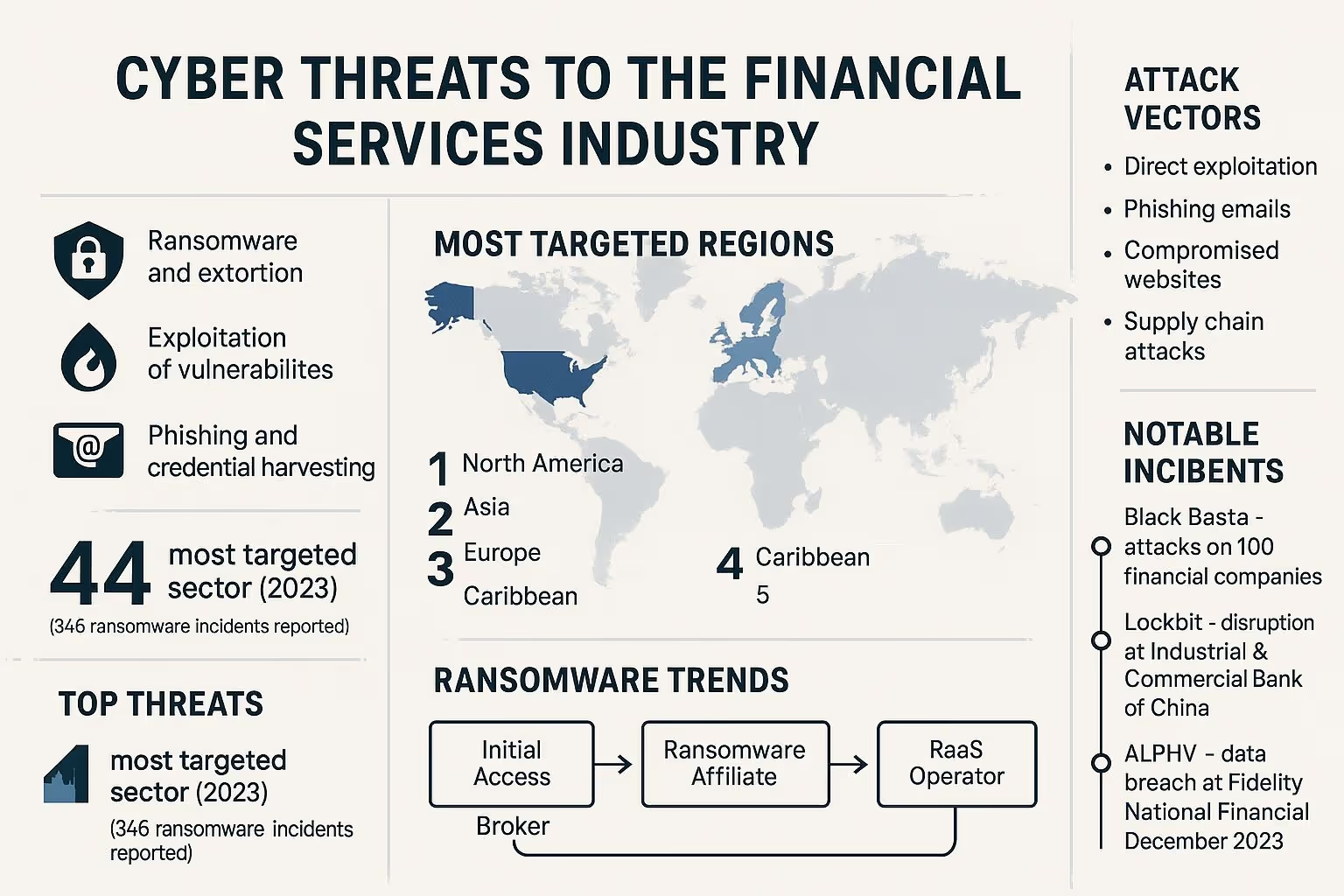
Cyber threats against financial services are rising rapidly. In 2023, the industry was the fourth most targeted sector for ransomware attacks, with 346 confirmed incidents in the US alone. The FS‑ISAC 2025 report warns that generative AI is amplifying fraud, scams, and supply-chain attacks.
For SCI entities, Regulation SCI expects policies and testing for capacity, integrity, and continuity. Keep change and test records that reference the external signal. New York’s 23 NYCRR 500 was amended in 2023 and ties incident response to business continuity.
Horizon scanning feeds ingest CISA’s Known Exploited Vulnerabilities catalog, FBI and CISA joint ransomware advisories, and sector alerts from FS‑ISAC. They also watch vendor security bulletins and urgent patches. KEV entries are a high‑priority input because CISA lists vulnerabilities with confirmed in‑the‑wild exploitation.
A KEV match without proof of patch status will not satisfy an examiner after an incident.
For example, let’s consider an SQL injection attack. Here a scan entry potentially triggers patching, external access checks, and data‑loss review for any managed file transfer systems. The record is linked to the CISA advisory.
10. Innovation & Product Development
Fedwire’s move to ISO 20022 was a structural change. The Federal Reserve executed a single‑day cutover on July 14, 2025, which means richer, structured payment data now flows through core systems at wire speed. This affects mapping, reconciliation, and any downstream control that keys off payment fields.
Horizon scanning tools treat this kind of dated network change as a first‑class signal. They pin the effective date from the source and surface the schema deltas. They also open product and ops checklists tied to that notice, so evidence lands in the same place as the rule link.
PCI DSS v4.0 shifted the landscape in March 2025 when several future‑dated requirements became mandatory. This pulled new authentication, logging, and risk‑analysis work into customer‑facing flows and vendor integrations.
The RTP network raised its transaction limit to 10 million dollars effective February 2025. This in turn unlocked high‑value use cases that had sat on wires. It forced updates to limits and fraud thresholds. Scanning tools now watch network bulletins for these jumps.
Platforms have changed the rules of engagement. Apple updated U.S. App Review Guidelines in May 2025 to reflect a court decision on buttons and external links. Their update affects copy and disclosures in finance apps. Google Play continues to police lending apps. In the United States, personal‑loan apps with APR at or above 36 percent are not allowed, and apps must display the maximum APR calculated under TILA.
Some pilots need a supervisory gate. The Federal Reserve’s Novel Activities Supervision Program (SR 23‑7) covers crypto, tokenization, and complex bank‑fintech partnerships. Horizon scanning feeds can tag any in‑scope feature and store the link to SR 23‑7 in the product file, with a short note on applicability and the approvals required.
Conclusion
Horizon scanning is the discipline of turning outside signals into dated, defensible decisions. When the record is clear, board reviews, audits, and exams run on facts. Not memory.
Key takeaways
- Use one register as the system of record. Each entry shows the source link and the owner. It also shows the due date and the proof of closure.
- Anchor decisions in the right rule set. UDAAP for conduct. TILA and Regulation Z for pricing and disclosures. EFTA and Regulation E for payments. ECOA and Regulation B for fair lending. Regulation SCI for market structure. NYDFS 23 NYCRR 500 and FFIEC handbooks for cyber and continuity.
- Keep scoring simple and tied to action. Proximity and time to effect are enough to start.
- Set triggers that cause action. A rule date opens a plan. A KEV match starts an emergency patch. A vendor deprecation starts a change freeze. A complaint spike starts a UDAAP review.
- Keep the evidence pack small and stable. Include the external notice. Include the decision record. Include the redline or the test result.
- Put compliance at the product and pricing gates. Sign‑off happens before launch or repricing.
Q&A
1) Who should own horizon scanning?
A small central function runs the register and the cadence. Business, legal, risk, and technology teams own their entries.
2) Tool or process. Which matters more?
Tools pull sources and route alerts. The value comes from ownership, thresholds, and closure proof.
3) How do we start without boiling the ocean?
Begin with a narrow scope. Take one rule feed. Add one cyber advisory source. Add one vendor bulletin source.
4) What evidence satisfies examiners?
Show the public notice. Show the decision record. Show the test or the redline.
5) How do we link scanning to third‑party risk?
Tag entries that name a vendor. A bulletin or a leak triggers escalation and a fallback drill.